Waiting on the platform for a morning train that was nowhere to be seen, he asked Meta’s WhatsApp AI assistant for a contact number for TransPennine Express. The chatbot confidently sent him a mobile phone number for customer services, but it turned out to be the private number of a completely unconnected WhatsApp user 170 miles away in Oxfordshire.
Tagged with security
Individuals will have to become their own chief security officer – finding a way to manage and control access to all of their digital assets, cloud services, social media profiles, personal communications and private devices. As our personal digital universes expand exponentially, so will the necessity of controlling our data and digital identities.
Children as young as 14 are making thousands of pounds a week as part of a global hacking network built around the popular video game Fortnite.
About 20 hackers told the BBC they were stealing the private gaming accounts of players and reselling them online.
"The email said that my password had been changed and two-factor authentication had been added by someone else. It felt horrible," he recalled.
Two-factor authentication meant his account could only be accessed by entering a code sent to an email address or app registered by the perpetrator.
You can learn how to use two factor authentication for Fortnite here
An academy has apologised to parents and pupils after a 16-year-old logged into a school laptop and downloaded pupils' personal data and shared it.
The boy, who attends Ormiston Rivers Academy in Burnham-on-Crouch, Essex, obtained the details of Year 11 pupils after using a teacher's laptop.
'Facebook has announced it will inform users if their accounts are being spied upon by any government.
In a note on Facebook, the company's security chief Alex Stamos said people would be notified if there is evidence their profile has been "targeted or compromised by an attacker suspected of working on behalf of a nation-state".'
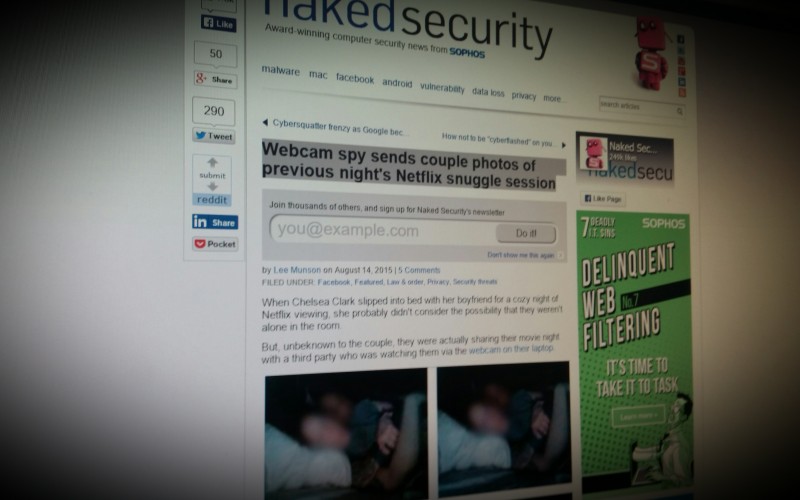
'When Chelsea Clark slipped into bed with her boyfriend for a cozy night of Netflix viewing, she probably didn't consider the possibility that they weren't alone in the room.
But, unbeknown to the couple, they were actually sharing their movie night with a third party who was watching them via the webcam on their laptop.'
Read more

Comments
make a comment