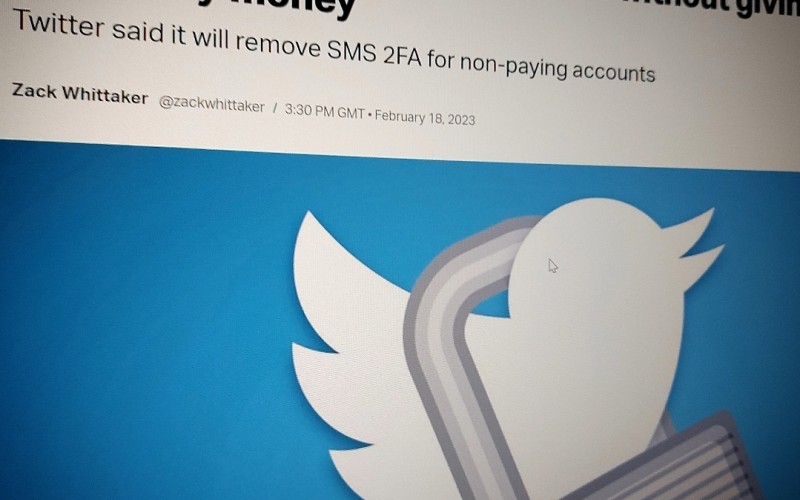
In a blog post, Twitter said that it will only allow accounts that subscribe to its premium Twitter Blue feature to use text message-based 2FA. Twitter users that don’t switch to a different type of two-factor authentication will have the feature removed from their accounts by March 20.
That means that anyone who relies on Twitter sending a text message code to their phone to log in will have their 2FA switched off, allowing anyone to access their accounts with just a password. If you have an easily guessable Twitter password or use that same password on another site or service, you should take action sooner rather than later.
Comments
make a comment